Ubuntu’s Unattended-Upgrades in Action
 I just performed a fresh offline install of Ubuntu Desktop 24.04.2, deliberately preventing any automatic updates during setup.
Shortly after logging in, I discovered that my VM was vulnerable to CVE-2025-32463, a local privilege escalation flaw in
I just performed a fresh offline install of Ubuntu Desktop 24.04.2, deliberately preventing any automatic updates during setup.
Shortly after logging in, I discovered that my VM was vulnerable to CVE-2025-32463, a local privilege escalation flaw in sudo.
Fresh Offline Install and Initial Findings
Vulnerable to CVE-2025-32463!
CVE-2025-32463: Overview
-
Affected versions:
sudo1.9.14 through 1.9.17 -
Fixed in: 1.9.17p1
-
Root cause: Mishandling of the
-R/--chrootoption that allows loading attacker-controlled shared libraries before performing privilege checks. -
Impact: Any user granted a sudo rule (even limited ones) can craft a malicious chroot environment containing a fake
nsswitch.confand a trojanized library, then execute arbitrary code as root.
Proof of Concept
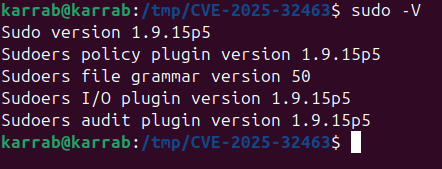
My test VM shipped with:
sudo --version
# sudo 1.9.15p5
I cloned and ran the publicly available PoC from my GitHub repository: CVE-2025-32463 PoC
git clone https://github.com/MohamedKarrab/CVE-2025-32463
cd CVE-2025-32463
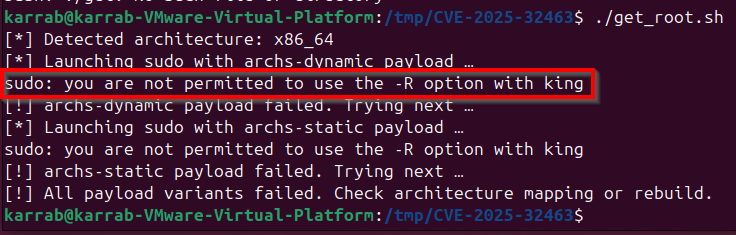
./get_root.sh
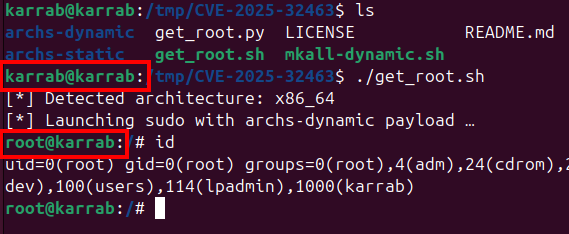
Upon execution, the script escapes to a root shell.
The Role of Unattended-Upgrades
Here’s the kicker: if I had installed Ubuntu with internet access enabled, this vulnerability would never have been exploitable on my system. That’s thanks to Debian’s Unattended-Upgrades service, which is enabled by default on Ubuntu Desktop and Server.
Unattended-Upgrades automatically downloads and installs only security-related package updates in the background, without any user intervention. Even though I never ran sudo apt update or sudo apt upgrade.
Verifying Unattended-Upgrades in Action
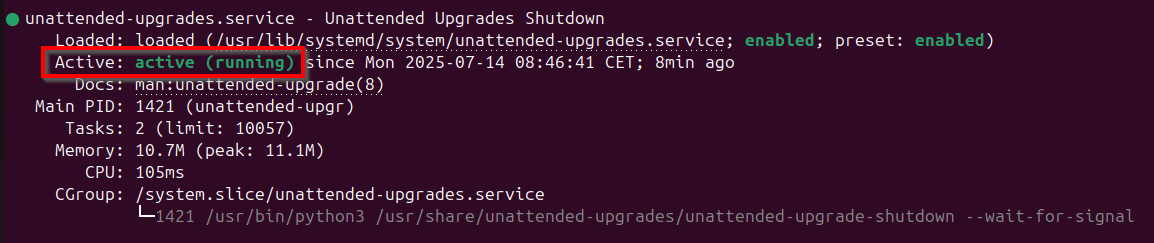
On a second Ubuntu installation that did have network connectivity, you can confirm the service is running:
systemctl status unattended-upgrades
Then inspect its logs to see which packages were auto-patched:
sudo cat /var/log/unattended-upgrades/unattended-upgrades.log
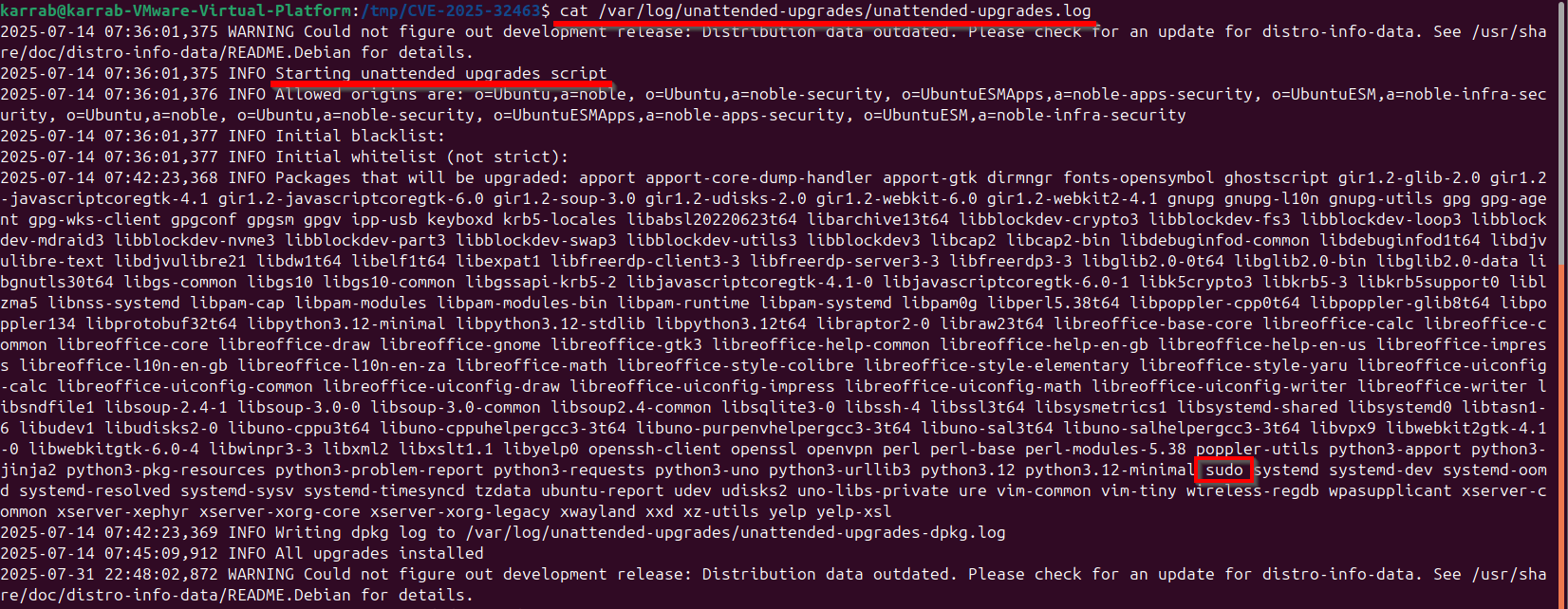 And of course, sudo is there!
And of course, sudo is there!
As you can see, the vulnerable version is replaced seamlessly, closing the exploit window.
Enabling or Tuning Unattended-Upgrades
If you want to ensure your system is always protected:
-
Enable the service (if disabled):
sudo dpkg-reconfigure --priority=low unattended-upgrades -
Review its configuration in
/etc/apt/apt.conf.d/50unattended-upgrades. Key options include:-
Unattended-Upgrade::Allowed-Originsfor which repositories to auto-patch -
Unattended-Upgrade::Mailto receive email notifications -
Unattended-Upgrade::Remove-Unused-Dependenciesto clean up old packages
-
-
Test in dry-run mode: Simulates what would happen without performing any actual upgrade.
sudo unattended-upgrade --dry-run --debug
Conclusion
By installing Ubuntu offline, I inadvertently sidestepped the very mechanism designed to protect my VM. CVE-2025-32463 highlights not only the importance of prompt patching but also the value of unattended-upgrades as a safety net. Always verify that your systems are configured to automatically receive and apply security fixes—your future self will thank you.